Can Cloudflare Hurt Your Sales or Turn Away Customers?

Cloudflare is one of the most common names when it comes to website protection, anti-DDoS gating, and content delivery via distributed network. Over the last decade, a lot of information – and misinformation – has been spread about the network. Some things people have said are false, and others may have been true but have changed in the years since. With so much to content with, it’s no wonder people research the answers before they consider buying in.
I’m going to go over one of the primary concerns with Cloudflare, which is whether or not it can potentially harm your ability to make sales or convert new customers. Before we begin, though, I’d like to talk about what this article is not.
This article is not an analysis of Cloudflare’s effect on SEO. For that, you want to turn to other authorities, at least until I get around to doing my own analysis. This case study is a pretty good one, for example.
I’m going to take a look at more direct issues with Cloudflare. Can it accidentally block legitimate traffic?
Can Cloudflare Block Legitimate Users?
I might as well not dance around it. Yes, Cloudflare can occasionally block legitimate users. However, it’s fairly unusual and it’s not likely to happen in an instance where it matters to a sale.
There are three instances where Cloudflare might be blocking something legitimate. The first is when they have enabled anti-DDoS mode and are aggressively filtering traffic. The second is when they’re blocking tools that legitimate users might want to use. The third is when the user is somehow malicious and unwitting. I’ll talk about each of these individually next.
The benefits of Cloudflare are strong enough that, even if it’s blocking a few customers, it’s generally worthwhile to use anyway. DDoS protection is just one benefit to their service in general; the CDN can be helpful for other reasons as well.
Anti-DDoS Blocking
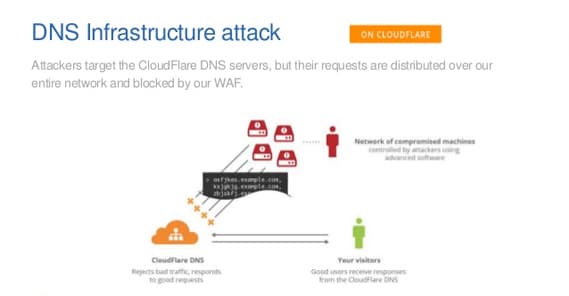
The first instance where Cloudflare might be blocking legitimate users is when your website is under a DDoS attack and it is filtering traffic aggressively to try to keep your server up and your website alive. It’s an example of killing a few to save the many, essentially.
Think of it like hunting. When the numbers of a certain animal exceed what natural predation and natural habitats can support, human hunting can help thin the herd. This reduces strain on the environment and brings nature back into a more self-sustaining balance. Wild, unrestrained hunting can destroy an animal population, but careful pruning of a species can keep it from driving itself extinct.
To apply the analogy to Cloudflare, think of your audience as the herd and your website as the environment. If the herd grows too large – during a DDoS – it destroys the environment, bringing your site down and killing the entire audience. You can’t make sales if no one can access your site, right? By carefully pruning out some of the traffic, Cloudflare can keep your site up and active. 99% of the traffic that is blocked is bad bot traffic, but some legitimate users may be caught in the net. Sure, you might lose a few sales, but nowhere near as many as you lose if your site is down entirely.
For the individual user, it’s certainly frustrating. How many times have you wanted to browse a site, only to be confronted with the Cloudflare block warning? The service attempts to provide a cached version of the site to browse while blocking is going on, but in my experience it rarely works. If a site protected by Cloudflare is under attack, and you can’t access it right away, it’s probably not going to happen until the attack is over.
Tool Blocking
The second case where Cloudflare might be blocking legitimate users and legitimate traffic is if those users or that traffic comes from a tool rather than the user directly. I have two specific examples here.
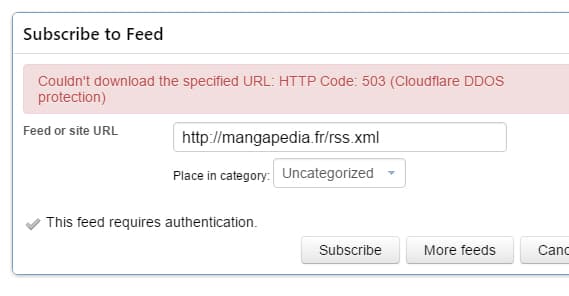
The first example is RSS. RSS readers check your site – specifically your RSS feed – on a regular schedule. Some might be hourly, some once a day, some on other schedules, but they all work the same. Any user who wants to keep up with your blog via RSS is going to be using an RSS reader of some kind to access it.
The problem is when Cloudflare decides that the RSS traffic is too bot-like and blocks it. You run into cases where the RSS reader never picks up new RSS data, for one reason or another. It’s common enough problem that people have gone out of their way to try to code bypasses and deal with the issue in various ways. Cloudflare is, of course, difficult to bypass for good reason.
How many people reading your RSS are going to convert into customers? It’s hard to say. Many of them might already be customers, looking to keep up with your blog. Others might eventually convert, but probably not from the RSS directly. Unless you can measure those specific numbers, it’s impossible to tell if you’re losing customers directly.
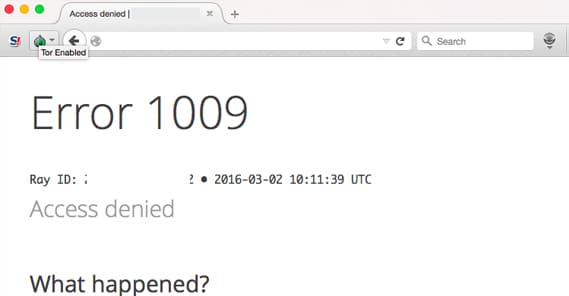
Another example is TOR. TOR is The Onion Router, a set of layered proxy connections that anonymize web traffic through a hazy cloud of redirects, as a way of adding security to web browsing. Your ISP can’t track your activities if they can’t tie your activities to your computer, right?
TOR has its issues, and I’m not going to dig into them right now. Suffice it to say that in some cases it’s not as anonymous as it claims to be. However, TOR is also often used for less legitimate traffic. There are two issues with this, and they both come down to how Cloudflare blocks traffic.
Cloudflare blocks traffic based on user agent and IP. TOR gives your traffic the information of whatever end point node you happen to be connecting through for that given session. Your traffic can come through a node that has been blocked for past abuses. Alternatively, you disable TOR, but your computer has been used as a node when you had it enabled, and your information is blocked.
Cloudflare has attempted to lessen the impact of using TOR, but there’s only so much they can do. If they lift all the blocking and filtering options, that tool will simply be used against them, and it makes it much harder to block specific bots.
Again, though, sacrificing a few users of specific tools in favor of keeping your site alive in the event of malicious traffic is generally a small price to pay. Unless you’re operating in a very narrow niche where 99% of your customers are users of such a tool, it won’t be that big of an impact.
Unwitting Maliciousness
Much like the case where your node in a TOR network is used as a pass-through for malicious traffic, other causes can lead to your IP being blocked. DDoS attacks are often committed through the use of a botnet, and botnets are generally composed of infected computer systems. When a computer gets the right kind of virus, it can be used as a slave to deliver traffic for a variety of reasons.
Tech-savvy users are going to keep their computers generally free of viruses and won’t likely be part of such a botnet. Less savvy users, however, abound. In fact, many of your customers – unless you’re in a high-tech, complicated and expert-level niche – will be less savvy users. The stereotype of your grandma’s computer needing disinfecting every family holiday is a real problem. If your grandma wants to make a purchase, she might find her computer blocked because a virus on it has been part of a DDoS botnet in the past.
It doesn’t even need to be a personal computer anymore, these days. Many botnets today are actually made up of various Internet of Things devices. Anything from a thermostat to a light bulb to a coffee maker can be infected and slaved to a botnet. After all, who thinks about updating the firmware on their light bulbs, or even considers the possibility of a smart bulb to visit a website?
Cloudflare might block the light bulb – which is one hell of a cyberpunk sentence to write, let me tell you – but they might also just block the IP the infected device is using. That will have the side effect of blocking your computer, even if your computer did nothing wrong. Grandma might not be using smart light bulbs, but a sufficiently smart thermostat or a coffee maker or a smart TV might be more plausible.
Again, this is something Cloudflare is working on preventing. This is where user agent blocking comes in handy. They can block devices that aren’t using typical browser user agents, but then, a corrupted device can spoof a user agent too. It’s all a complex and frankly obnoxious arms race. Plus, you don’t want to block those devices if, say, you’re the one providing the firmware updates.
Benefits Worth the Risk
With the chances of blocking legitimate traffic – and the suspicion that Cloudflare can hurt SEO in a few configurations – is it worthwhile to keep using the service? I’m of mixed opinion.
On the one hand, a DDoS is obviously a bad thing. If you’re under attack, using something to filter traffic and keep your server alive is a good idea. Site downtime is infinitely worse than a few blocked users, especially when you have no way of knowing whether or not those users are actually interested in becoming customers. Cloudflare isn’t the only game in town, but since they’re one of the most visible brands, they take a lot of flak for their competitors.
On the other hand, Cloudflare’s services can be beneficial in other cases. One of their primary uses is as a content delivery network, and using a CDN can be a benefit to SEO. Faster load times are beneficial to search ranking, and a CDN can speed up a slow loading site if your server can’t handle media as quickly as the CDN can.
At the same time, there are other CDNs. If you want to benefit from a CDN but don’t feel the need for DDoS protection, you can invest in something like Amazon’s CDN or Akamai. Of course, that can leave you high and dry if a DDoS does come knocking, so you need some kind of disaster management and recovery plan.
In general, I would say that using a CDN is always going to be a benefit, though you should focus on using one that servers your local region. Cloudflare users have had issues where the IP of the CDN-served content came from outside the usual region and thus took an SEO hit.
Using Cloudflare specifically can be a good idea if you believe your site is at risk of a DDoS attack, though there are other DDoS protection apps available if you don’t trust a tainted name.
If nothing else, if your business is not in a precarious position, you can test Cloudflare with little repercussion. Make an announcement on your site and on your social media that you will be testing Cloudflare, and ask that any users who experience issues come forward and help you troubleshoot. If you do find some issues, you can disable Cloudflare and cancel the experiment. If, on the other hand, you have no issues, Cloudflare can work just fine for your business.
 ContentPowered.com
ContentPowered.com